How do you get the Kc from a SIM card?
Sounds kind of like a magical question, right? It is interesting that there are pretty much no guides on this topic, because for any GSM-debugging you need to have the so called Kc (pretty much a session key) that was used to encrypt the traffic sent over the air.
So let’s get started: there are as many as 4 ways to do this, and some other that I tried and don’t actually work, so let’s see:
Ways that work:
1. BlackBerry Engineering Screen
This is quite an easy catch: pretty much on all of the BlackBerries you can enable the so called “Engineering Mode” which will simply show you the current Kc. Not much of fun, but a reliable, good way to do it.
TESTED: YES (as shown by Karsten Nohl for example at BlackHat 2010)
WORKS: YES
2. OsmocomBB Mobile App
Now, this one is quite a tricky one, because setting up OsmocomBB already requires quite an amount of work, but once you have it up and running AND you are lucky with the cables and the code (which is not usually the case) you can simply run the mobile app and then use the telnet interface to get the Kc:
1. Upload layer1 to your phone
2. Run mobile -i 127.0.0.1
3. telnet 127.0.0.1 4247
After that simply say:
show subscriber 1
At the top you should see the Kc printed.
TESTED: YES
WORKS: PARTIALLY (I was able to get the Kc, but the mobile app itself wasn’t working for me, so I couldn’t place a call or send an SMS just to try out if I have the right Kc or not)
3. AT+CSIM Command
This one is the eldest and most well-known command: some phones allow you to use one of  the standard-defined-but-not-always-implemented AT command AT+CSIM which let’s you to send raw APDUs (=”commands”) to the SIM-card via the modem. The amount of phones supporting this is very limited, according to some people older Siemens and Alcatel phones let you do this. Also older iPhone’s (3GS/3G/2G) let you do this if you are jailbroken (you need to install minicom from Cydia then connect to the device /dev/tty.debug). Newer iPhone’s don’t really let you do this, iPhone 5 owners – we all are out of luck.
The command you would like to send is something like this:
 Sample run:
AT+CSIM=14,"A0A40000026F20" +CSIM: 34,"000000096F2004001100BB010200009000" OK AT+CSIM=10,"A0B0000009" +CSIM: 22,"E0940FC09AEFA000009000" OK
Again, you find the last Kc used here: E0 94 0F C0 9A EF A0 00 and also the key sequence number: 00
From:Â http://openbsc.osmocom.org/trac/wiki/A5_GSM_AT_tricks
TESTED: NO
WORKS: PROBABLY
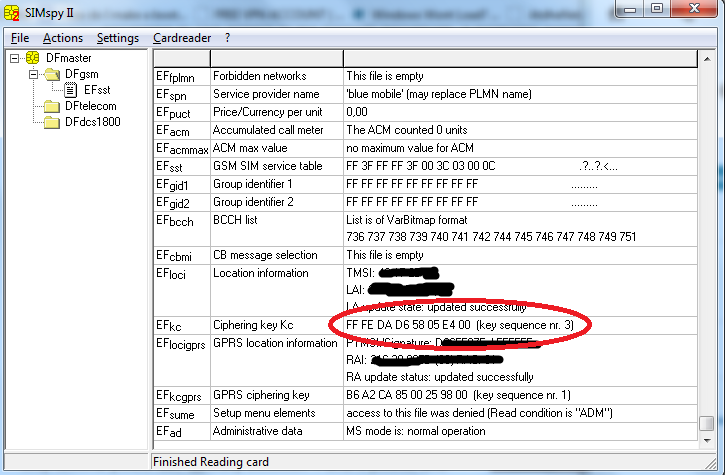
4. Using a SIM-card reader/Smart Card Reader
Some people said on the A51 mailing list that by using a simple SIM card reader they were able to extract the last used Kc from the card. I am not sure about this, but it sounds reasonable and the people who wrote about were quite convincing.
UPDATE: I tried this method using a simple PC/SC cardreader (exact model: Omnikey CardMan 5321 – it is great because it has both RFID and contact-smart card reading interfaces) and I am happy to tell you it works! Running SIMspyII after I inserted the SIM-card into the reader revealed the Kc and also everything else stored on the SIM card (I already turned off PIN-code verification for the card, not sure however how having a PIN code would change the procedure, but I assume the SIMspyII program has support for PIN-codes).
The only interesting part is that the SIM-card itself is a lot smaller than a standard smart card, so you need to either take the reader apart and insert the card alone, or use the plastic card the SIM-card came with, or use an old credit card.
Also there are some rumors that you can’t power down your phone because it would erase the Kc from the SIM card so you need to pull the battery out. According to this mailing list thread you don’t need to do that because according to GSM specification the Kc should remain on the SIM card even if the phone is poweered down (Harald Welte). According to my experience this is true.
TESTED: YES
WORKS: YES
Other ways which don’t work:
1. Nokia DCT3 FBUS Connection:
Sounds like an ideal setup: you use an old Nokia DCT3 (3310/3410 etc.) and an FBUS cable. Using dct3-gsmtap from OsmocomBB you would be able to sniff all the packets the phone receves/sends, and also all communication between the phone and the SIM-card. Since we know the command we are looking for (see above, A0 A4 …) we can easily find the Kc – one would think. Sadly that’s not the case, Nokia’s engineers closed this possibility: after the command the next packet we can see coming from the SIM card is an empty packet. This causes Wireshark to say Malformed packet and shows no data in it – which is totally right, after looking at dct3-gsmtap’s output you can observe the following:
SIM: 0xA0 0xA4 0x00 0x00 0x02 0x7F 0x20 SIM:
So, empty message coming back.
TESTED: YES (Nokia 3410 + FBUS cable)
WORKS: NO
I will update this list as soon as I find new ways to extract the KC.